Enhance your space with top-quality tiles, granite, and stone solutions.
Perfect for homes, offices, and commercial spaces.
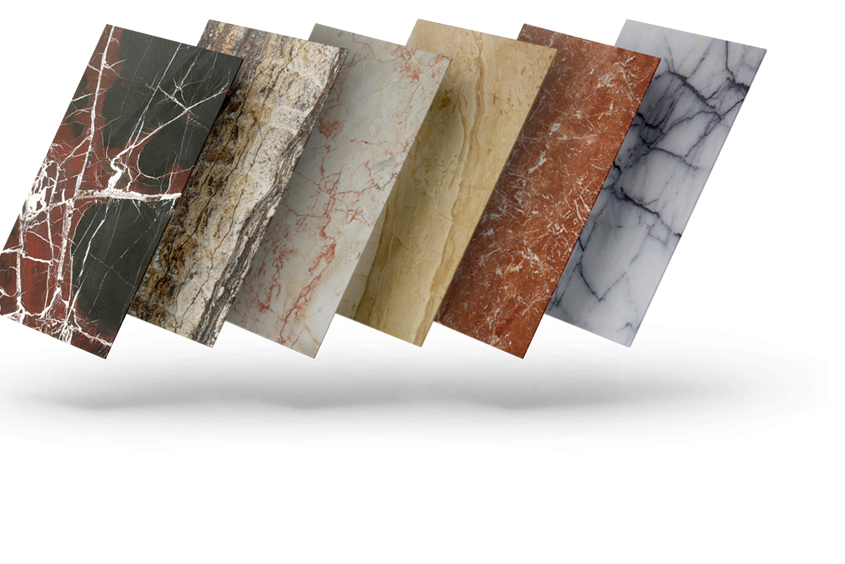
LARGEST TILES & MARBLES STOCKIST IN UAE
TIMELESS ELEGANCE FOR EVERY PROJECT
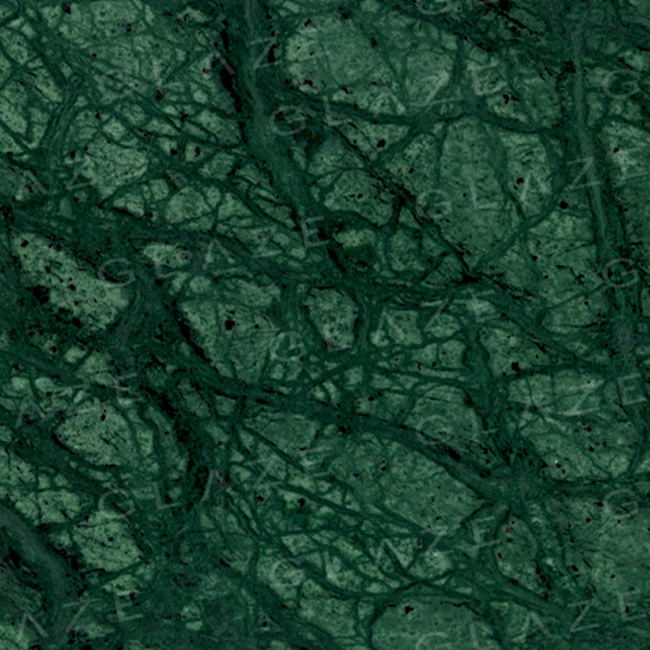
Discover high-quality ceramic, porcelain, and natural stone tiles
designed for durability and style
designed for durability and style
QUALITY MATERIALS, EXCEPTIONAL DESIGNS
From modern interiors to classic aesthetics,
we offer the perfect surface solutions for every need.
we offer the perfect surface solutions for every need.